I tested "dummy" and did not work
Introduction to Linux interfaces for virtual networking
Code: Select all
sudo ip link add eth0 type dummyAlso tested "macvlan" as mentioned here Create a virtual network interface using the iproute2 "ip link" command with a spoofed MAC address
Code: Select all
ip link add name vif0 address 5E:FD:E6:69:83:DF link eth0 type macvlan
ip addr add 192.168.104/24 brd + dev vif0
ip link set dev vif0 upCode: Select all
netstat -i
Kernel Interface table
Iface MTU RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg
eth0 1500 9350 0 0 0 4498 0 0 0 BMPRU
lo 65536 288 0 0 0 288 0 0 0 LRU
tap_tap 1500 298 0 0 0 256 0 0 0 BMRU
vif0 1500 394 0 0 0 477 0 0 0 BMPRUIs the network device in promiscuous mode?
Code: Select all
grep -r 'promiscuous' /var/log/kern.log
Feb 16 11:00:50 server-fra kernel: [416435.753728] device eth0 entered promiscuous mode
Feb 16 21:17:14 server-fra kernel: [453419.230297] device eth1 entered promiscuous mode
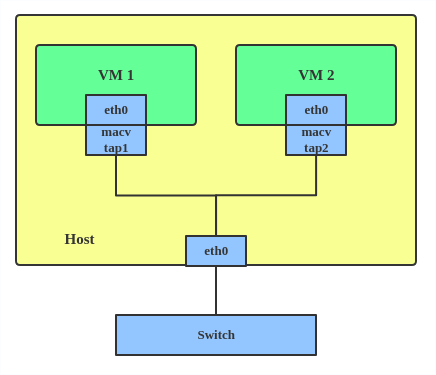
Feb 17 11:13:06 server-fra kernel: [503570.743742] device vif0 entered promiscuous modeAnd as long as I know tap devices operate at layer 2 so SE can bridge to a tap device (e.g. tap_tap) via Local Bridge
Stopping a SE server or making a HUB offline removes these tap devices (I know we can use "PostStartExec" with systemd but it does not have a use case for my condition)
Beside asking the VM provider to add a new interface (NIC) to the VM, is there any ways to make it work?
Also please correct me if I have misunderstood any concepts mentioned above.
Since I am not sure which type is the right way to use or even is it possible or no, maybe I should look at "MACVTAP/IPVTAP"
Regards
